
ICT Policy
1.0 INTRODUCTION
UTHM is committed to creating an information and communications technology (ICT) environment that meets the needs of customers. UTHM is responsible for providing an ICT environment that can contribute to the achievement of academic excellence through efficient and effective administration. Adequate and up-to-date ICT facilities are essential to ensure quality teaching and learning to produce highly competent graduates. In addition, ICT facilities will be able to aid in the work of innovation, research and development to achieve the goals of the university as well as increase quality publications of the members of the university who practice ICT culture.
2.1. The administrator password is the password for the system administrator.
2.2. Internet Protocol (IP) Address is the address given to an ICT hardware to communicate in a computer network and the internet.
2.3. An antivirus is a software used to prevent, detect and remove computer system intruders, including computer viruses, computer bugs, and others.
2.4. Attachment/email attachment is a computer file (attachment) sent together with an electronic mail message.
2.5. An Automatic Voltage Regulator (AVR) is an electrical appliance that automatically stabilises electrical voltage.
2.6. Backup is the process of backing up by making a copy of the data where it is used for re-accessing the data in the event of damage/loss of the original data.
2.7. Backup System is a backup/supporting system available to backup the main/master system in the event of failure of the main/master system to function.
2.8. Backup tape is a tape-shaped piece of hardware used to store a number of data storage for reference, support, or exchange.
2.9. CDO is Chief Digital Officer or the university’s Chief Digital Officer.
2.10. A Client-server is a user to a server through a network system involving services provided by a resource provider known as the server and the applicant of that service known as the user.
2.11. Daemon is a computer programme that is executed behind the scenes without user interaction.
2.12. A depositor is an institutional repository of documents.
2.13. Downtime is the period of time a computer system cannot be used.
2.14. External storage is storage outside a computer that can store information in a form that is processable to a computer.
2.15. A firewall is security software or hardware intended to protect a computer system or network from intrusion (e.g., hacking).
2.16. Freeware is free software distributed by the software developer.
2.17. Hacking is the process of attempting to intrude through various means to use a computer system illegally.
2.18. ICT (Information and Communications Technology) is defined as activities related to the collection, processing, storage and dissemination of data using computerised information systems that include aspects of hardware, software, network/communication and system application development and other communication equipment.
2.19. Install is the act of installing hardware or software into a computer system.
2.20. An Intrusion Detection System (IDS) is software, hardware or a combination of both to monitor the network and system activity that is suspicious and is likely to cause failure to the system or network.
2.21. An Intrusion Prevention System (IPS) is hardware/software that monitors and blocks suspicious activity in the network.
2.22. Integrity is a concept of consistency in actions, values, means, measurements, principles, evaluations and outcomes.
2.23. JKICTU is the University ICT Committee.
2.24. JPPTM is the Information Technology Evaluation And Procurement Committee.
2.25. JPPS is the System Development Deciding Committee.
2.26. Academic ICT Requirements is the ICT environment that supports the university’s academic activities.
2.27. Malicious code is a code built to corrupt data and operating systems.
2.28. Letterbomb is an email message that contains data to damage the data, the user’s computer and the network involved.
2.29. A lightning arrestor is a hardware used by electrical and telecommunication power systems to protect the insulation and conductors of the system from damage due to lightning.
2.30. A Mailbox is a file owned by a user in a computer that receives electronic mail readily stored for the user to read. It also contains electronic mail address information in private lists or electronic mail server lists.
2.31. Offensive is another act of hacking used by cyber hackers when an attack is made on a system or network.
2.32. OKU (Persons with Disabilities), according to the Persons with Disabilities Act 2008, is a person with a long-term disability in terms of physical, mental, intellectual or sensory who, when faced with various obstacles, may not be able to participate fully and effectively in society.
2.33. Pattern is the same or repeated type of an event or object, sometimes referring to an element or a set of objects.
2.34. The owner is an entity that can approve or deny access to data and is responsible for the accuracy and integrity of the data and is constantly updated.
2.35. Incidental Use is the use of university resources other than for official purposes or duties.
2.36. Bugs are errors contained in a software.
2.37. The ICT environment includes infrastructure, hardware, software, services, training, and maintenance.
2.38. ICT Policy is a guiding policy for providing, managing, implementing, and improving ICT facilities.
2.39. Postmaster is a list of electronic mail contact addresses connected to a network. Sometimes, it is known as an electronic mail system administrator.
2.40. A power socket is an electrical connection device to enable the electric connection so that it can function to channel electrical power in a building.
2.41. A Repository is a location for storage, typically for security and conservation.
2.42. Institutional Repository is a place to collect, store and disseminate the scientific results of an institution via an online channel, especially for a research institution or university.
2.43. Root is the system administrator-level access that can give full control over a server.
2.44. A scan engine is a software used to check for or detect viruses.
2.45. Shareware is software that is shared and distributed for free for a period set by the system developer.
2.46. A smoke detector is a hardware for detecting smoke, primarily as a fire detector.
2.47. Spam is emails that send irrelevant messages, resulting in cybercrime incidents.
2.48. The Super-user is the system administrator.
2.49. A surge arrestor is a hardware installed between a communication device and a coaxial cable connector or between two communication devices to protect the equipment from being damaged due to high voltage.
2.50. Full text is the whole document accessible, not just the abstracts or excerpts of the document.
2.51. Green ICT Technology refers to the practice of production, use, and disposal of computers, servers, and accessory devices such as monitors, mouse, printers, and network equipment effectively and efficiently with minimal or no impact on the environment.
2.52. Trunking is plastic or metal hardware used as protection and passage to the wire/cable.
2.53. Uninterruptible Power Supply (UPS) is a type of electrical equipment that provides an electrical power supply for support in the event of a power system failure, usually for emergency purposes by using an emergency power system or an available generator.
2.54. Computer viruses are programs that can replicate themselves and then spread from one computer to another for malicious purposes.
This policy serves as a guide to the university to provide and improve ICT facilities to achieve academic excellence and management efficiency.
The objective of this ICT Policy is to ensure that the followings are implemented, namely:
4.1 ICT planning is in line with the mission and vision, as well as the direction of the university.
4.2 The procurement of ICT is in accordance with the set standards and cost-effective.
4.3 The university’s ICT facilities are managed and maintained efficiently.
4.4 ICT security controls are enforced in accordance with procedures.
4.5 The use of ICT complies with ethics and rules.
4.6 The implementation of ICT culture for all university members.
4.7 Provision of the latest e-learning infrastructure.
5.1 To achieve the aims and objectives of the ICT Policy, UTHM sets the basic principles as follows:-
a) Administrative ICT Facilities
i. All Heads of PTJ:
a. Category of Academic Staff
Allocated with a personal computer (PC) and a printer.
b. Category of Non-academic staff (Administration)
Allocated with a personal computer (PC), a laptop, and a printer.
ii. All permanent/contract administrative staff from the management and professional groups are allocated with a personal computer (PC) and a printer, subject to the current university allocations.
iii. The provision of laptops to the permanent administrative staff from management and professional group, as well as from support group is subject to the current circular of the university.
iv. Each Responsibility Centre (PTj) is equipped with the requirements as the followings, subject to the current allocation of the university:
a. Adequate personal computers (PC).
b. One (1) colour printer.
c. One (1) multifunction printer.
d. Laptops for administrative use with a 1:5 ratio of laptops to administrative staff, subject to a minimum number of 1 and a maximum of 5 laptops.
e. Printers for administrative use with a ratio of printers to the administrative staff of 1:5 subject to a minimum number of 1.
b) ICT Facilities for Academic Staff and Students
i. All permanent academic staff are allocated a Notebook/Tablet/PC and printer via Baucar Bantuan Komputer Riba for the university’s academic staff.
ii. All contract academic staff are allocated a laptop with a 1:1 ratio, including a printer. Allocation of black ink, subject to the current university allocations.
iii. Provision of ICT facilities for post-doctoral and Tutors requires a letter of support from the Head of PTj.
iv. Computer facilities are provided to full-time students with a 1:5 target ratio.
c) ICT Infrastructure
i. Each PC is equipped with basic software such as an operating system, word processor, spreadsheet, presentation software, web browser, and antivirus for academic and administrative purposes.
ii. All Lecture Halls/Lecture Rooms/Seminar Rooms/office spaces and any space that conducts administrative, teaching and learning activities will be provided with computer network facilities and internet access.
iii. The lecture halls/rooms are equipped with e-learning facilities and other facilities as needed.
iv. Provides the infrastructure that supports multimedia-based teaching and learning facilities and courseware.
v. Provides the latest digital library facilities.
vi. Provides infrastructure to support the ease of use of automation systems (e-management).
vii. Provides software and hardware for video conferencing with the latest equipment.
viii. Each user is given broadband facilities that suit current needs and technology.
ix. The computer system operates 24 hours a day with minimal downtime.
x. PTj may provide printer facilities in the laboratory if needed.
d) ICT Infostructures
All system development required by any PTj must obtain approval from JKICTU for the purpose of coordinating technical requirements such as database, integration, infrastructure, and other related conditions.
i. Prepare and develop the latest application system based on the needs of the university.
ii. All internal system development required by any PTj are required to obtain:
a. Verification from JPPS and
b. Approval from JKICTU.
iii. All outsourced system development/procurement required by any PTj must obtain;
a. Endorsement from JPPTM, and
b. Verification from JPPS, as well as
c. Approval from JKICTU.
e) General
Staff who have completed their service at UTHM or are on leave for more than three months are required to return the ICT facilities that have been allocated.
5.2 The university, through JKICTU, can consider applications for ICT facilities other than those mentioned above if needed.
5.3 To create an ICT environment to achieve academic excellence and administrative efficiency, the university needs to provide adequate allocations to fund the procurement of ICT infrastructure and the development of system applications.
5.4 Staff who retire and have been provided with laptops during their period of service will be given the ownership of the laptop as a token from the university, subject to the university circular in force.
5.5 The hardware and software for staff and students with disabilities (OKUs) must comply with the guidelines issued by the university.
5.6 Comply with the website management based on the Circulars and Guidelines issued by the university and the Government.
6.1 Scope
This policy is applicable in UTHM and all UTHM branches which only covers matters related to ICT.
6.2 Responsibilities
The governance structure of university ICT management is shown in Figure 1.0.
Figure 1.0: The Governance Structure of University ICT Management
6.2.1 Executive Committee
The university committee that determines the implementation of university administrative and financial management policies.
6.2.2 Chief Digital Officer – CDO
a) CDO Appointment
i. The Vice-Chancellor shall appoint a University CDO from any University Officer who, in his opinion, is appropriate to carry out the duties and functions as a CDO.
ii. An officer who has been authorised to carry out such duties may, by written instrument, delegate such authority to any other officer for a period not exceeding seven (7) working days or any period as may be allowed by the Vice-Chancellor.
iii. If the CDO cannot perform any of the functions of his office for a long period due to illness, leave or any other reason, any other suitable University Officer may be appointed by the Vice-Chancellor to carry out the duties of the CDO.
b) The role of the CDO
The CDO will perform its roles as the followings:
i. To be a leader of change through the alignment of UTHM’s ICT Strategic Plan (ISP) with the requirements of the UTHM Strategic Plan and the Public Sector.
a. Spearheading UTHM’s ICT Strategic Planning; and
b. Strengthen UTHM ICT governance.
ii. To be a leader in Strengthening Global Policies, Standards, and Best Practices
a. Spearheading the adoption of Enterprise Architecture (EA);
b. Leading the adaptability of rules/policies/standards/best practices in the implementation of the Electronic Administration System; and
c. Leading the implementation of ICT shared services in UTHM.
iii. To be a leader of ICT Acculturation in the UTHM Service Delivery System.
a. Leading the alignment of UTHM’s ICT program.
iv. To be a leader in innovation through electronic government applications, infrastructure, and ICT security
a. Identify new generation services; and
b. Leading the information sharing towards cross-agency services.
6.2.2 UNIVERSITY ICT COMMITTEE (JKICTU)
JKICTU plays a role in policy-making, setting direction and strategies to achieve the university’s ICT goals, including enforcement, compliance, and monitoring of the ICT Policy.
The Information Technology Center acts as the Secretariat.
The job scope is as in Appendix 1(Click here).
6.2.3 INFORMATION TECHNOLOGY EVALUATION AND PROCUREMENT COMMITTEE (JPPTM)
JPPTM was established at the Information Technology Center to assess and recommend technical specifications for the ICT procurement application of PTj. JPPTM is responsible towards JKICTU. The job scope is as in Appendix 2(Click here).
6.2.4 SYSTEM DEVELOPMENT DECIDING COMMITTEE (JPPS)
JPPS was established to determine the priority in the development of new systems and upgrading existing systems. The Information Technology Center acts as the Secretariat, and JPPS is responsible towards JKICTU. The job scope is as in Appendix 3(Click here).
All ICT hardware, software, and equipment provided must have the following features:-
7.1 It comes with the latest version of technology, incorporating the characteristic of green technology and have the ability to be upgraded.
7.2 ICT hardware and software must have connectivity with the Local Area Network (LAN), Wide Area Network (WAN) and the existing computers.
7.3 Able to transfer data and information from one computer/device to another computer/device.
7.4 It enables internally developed computer systems.
7.5 It must be user-friendly and requires only minimal training.
7.6 Must be compatible with the existing ICT systems.
7.7 The software used must have a valid license.
7.8 Able to comply with legal requirements, including matters relating to employee health, security issues and software copyright.
8.1 The ICT planning must align with the National ICT agenda and meet the policies, rules and guidelines determined by the Government of Malaysia.
8.2 The ICT planning must meet the functions and needs of UTHM in teaching, learning, research, publication, consulting, administration and management.
8.3 The ICT requirements for academics and administration are planned and implemented collaboratively between PTj and the Information Technology Center.
8.4 The Information Technology Center is responsible for planning and implementing ICT requirements, and it must be certified by the JKICTU.
8.5 The ICT planning in all PTj must be submitted to JTPTj to be certified by JKICTU before its implementation.
9.1 The owner of the institutional repository is the UTHM library.
9.2 The management and administration of the repository system is a joint effort of the library and the Information Technology Center.
9.3 The institutional repositories include:
9.3.1 Books
9.3.2 Thesis/Dissertation
9.3.3 Articles/Periodicals
9.3.4 Project Paper
9.3.5 Lecture Notes
9.3.6 Reports
9.3.7 Slides/Videos/Images
9.3.8 Software
9.4 All repository materials must be entirely digitised (full text).
9.5 All repository materials must be accessible by:
9.5.1 Staff and Students: Full-text accessibility.
9.5.2 External Membership: Full-text accessibility.
9.5.3 Public Users: Abstract accessibility.
9.6 Staff and students or any PTj must submit the work (Refer to items 9.3.2 and 9.3.4) in digital form to the library.
9.7 Staff and students must submit the work (Refer to items 9.3.1, 9.3.3, 9.3.5, 9.3.6, 9.3.7) in digital or printed form to the library.
9.8 Copyright-related issues are subject to the existing laws, acts and regulations.
9.9 The university is not responsible for any copyright infringement committed by the depositor.
10.1 Applications for procurement of ICT requirements, including upgrades, replacements, and repairs, must be forwarded to the PTj’s Quotation Technical Deciding Committee (JTPTj).
10.2 JTPTj will review the technical specifications and then forward the application to JPPTM using the Equipment Specification Approval Application Form together with the procurement specifications. The application form is as in Appendix 4(Click here).
10.3 JPPTM will make an assessment before verifying it for approval. If the procurement value is worth RM 200,000.00 and above, verification by the JKICTU is needed.
10.4 If the technical specification has been approved, the following procurement procedure is according to the existing procedure.
10.5 All contract agreement documents must be reviewed by the UTHM Legal Unit before being signed by the PTj and the supplier.
10.6 A copy of the signed contract agreement document shall be submitted to the Treasurer Office and the Legal Advisor Office.
10.7 The procurement of laptops, personal computers (PCs), printers, and toner/cartridges is under the responsibility of the Information Technology Center, except for the procurement using research grants, through development projects, and the equipment directly connected to the machines.
10.8 The ICT procurement process flow chart is in Appendix 5.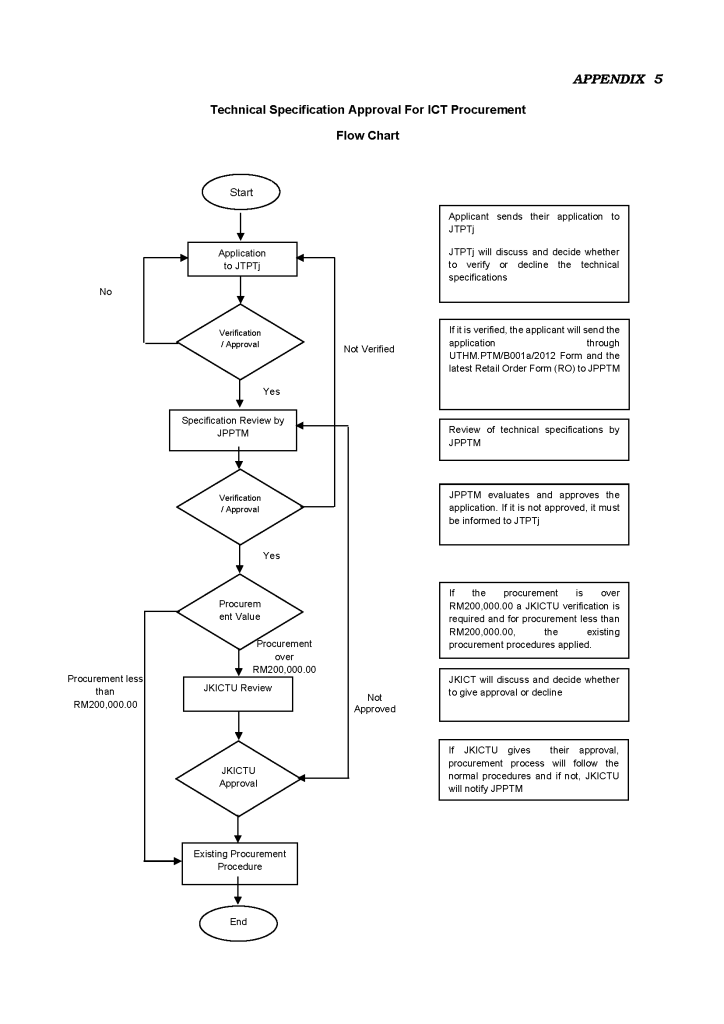
11.1 All procurement of hardware, software, and supplied equipment must have a detailed maintenance schedule provided by the equipment supplier. The maintenance schedule must be adhered to and monitored by the relevant PTj as long as it is still within the warranty period. The maintenance and repair of hardware, software, and networks that have passed the warranty period, including procurement made by PTj, must be notified to the ITC for centralisation purposes. The monitoring maintenance must also be done on a scheduled basis by ITC.
11.3 All hardware maintenance is carried out in accordance with the ICT Equipment Maintenance Procedure based on the user complaints (PSR-14) registered under MS ISO 9001: 2000.
In ensuring that university members are proficient in ICT, several training policies have been devised as follows:
12.1 New staff should be exposed to the university’s systems and applications.
12.2 Every staff must undergo ICT training subject to the University Training Policy or University Training Circular in force.
12.3 To provide specific training to staff according to the service scheme and job scope.
12.4 To provide exposure to students related to the latest technology, applications, and ICT skills.
12.5 Courses/training may be offered to external parties; are subject to university rules.
The installation, placement, use, and care of ICT equipment should follow the security procedures based on the ICT Security and Ethics Guidelines.
14.1 All disposal of ICT equipment must be supported by JPPTM using the form as in Appendix 6(Click here), before being forwarded to the Disposal and Loss Committee (JKPK).
14.2 The disposal process of ICT equipment is according to the Laboratory Equipment Management Procedure (PSR-18) registered under MS ISO 9001 with reference to the Work Instruction for the Disposal of Equipment/Materials Process (AK/04).
14.3 For the purpose of security and confidentiality of the university’s information, all hardware that has data storage must be copied to a different data storage and the data stored on the hardware storage must be deleted before disposal.
15.1 Centralisation is the process of placing ICT equipment for the general use of university members as determined by the university’s top management.
15.2 The centralisation of ICT equipment is a measure to further increase the level of usage and efficiency while reducing costs.
15.3 Centralisation of ICT equipment is done to ICT equipment that can be used, such as computers, software, printers, and other ICT equipment.
15.4 The implementation of the centralisation of ICT equipment is the responsibility of the Information Technology Center.
16.1 Review and amendment of the university’s ICT policy may be made from time to time as required with the approval of the university’s Board of Directors.
16.2 This ICT policy shall be effective from the date it is approved by the university’s Board of Directors.
16.3 This ICT policy should be read together with;
i. Policy for Giving Computer Vouchers to UTHM Administrative Staff and Academic Staff. (Dasar Pemberian Baucar Komputer Kepada Staf Pentadbiran Dan Staf Akademik UTHM),
ii. Consumer Safety and Ethics Guidelines as well as
iii. Circular or other policies on ICT management of UTHM in force.
17.1 UTHM Ownership
a. All ICT facilities and services provided by the university are the absolute property of the university except for the ICT equipment purchased through the Baucar Bantuan Komputer Riba (BBKR) method.
b. The university gives the right of ownership of ICT equipment to the staff who use BBKR and is responsible for maintaining and replacing damaged/lost equipment using their own financial allocation.
c. However, UTHM holds ownership of the ICT equipment if the staff uses the BBKR with the computer loan service. The staff will attain the ICT equipment ownership after the entire loan is paid.
d. ICT hardware and software that are the property of UTHM must be affixed with the sticker “Property of UTHM”.
e. All electronic files produced, printed, sent and received, or stored on hardware/computers owned, rented, or administered under the management and the control of UTHM are the property of UTHM unless it is proven otherwise, including electronic files related to official duties at UTHM that is found on ICT equipment purchased through the method of Baucar Bantuan Komputer Riba (BBKR).
17.2 Personal Ownership
a) Users who use the services, ICT facilities, and networks at the university through personal ICT equipment are given permission and must comply with the imposed ICT Policy.
b) The university is not responsible for any misuse committed by the users.
c) Action can be taken towards the users under any act in force if there is a complaint related to the staff’s misconduct involving the act.
18.1 Incidental Use
a) Incidental use of the university’s ICT resources is limited to the university’s mission and activities only.
b) Eligible users are given access to support the teaching and learning process, performing duties as staff or other official or university-approved activities only.
c) Any incidental personal use shall:
i. Not causing any measurable costs to the university.
ii. Not violating the university’s policies or laws.
iii. Not exposing the university to unnecessary risk.
iv. Not interfere with the performance of the duties or responsibilities as university staff.
v. Not interfere with the performance of infrastructure & networks, infostructures, and users.
d) The storage of electronic files or documents stored in the university’s system must be in minimum file size.
e) All files and documents, including users’ personal files and documents, belong to the university and can be accessed based on the requirements and regulations of the university.
18.2 Compliance and Violation of ICT Policies
a) This policy must be complied with by all users in UTHM, and it has been put together based on the suitability of UTHM aligned with the Government Acts.
b) Formal complaints about ICT rules or policies violation can be made through the online complaints system provided.
c) The university’s ICT policy must comply with the legal or regulatory requirements related to the Government Acts.
18.3 Actions and punishments
a) Preliminary action for any critical case such as a threat to the security of an individual, physical or information, can be taken through the temporary suspension of the rights or privileges of users to ICT resources.
b) The type of action or punishment when an offence can be proved will be decided by the University Disciplinary Committee or its equivalent committee.
c) Failure to comply with all instructions relating to ICT’s physical security, security of classified documents/information and/or protection of personal data resulting in loss, harm, or destruction, may result in the individual involved being subject to disciplinary action and/or surcharge action as it is deemed appropriate. The university also reserves the right to take legal action against the individuals involved if it is deemed appropriate and reasonable.